Secure Cipher Suites and TLS
TLS
As of writing (July 2021), there is really only one widely supported, secure protocol for establishing secure communications on the Internet -- TLS 1.2.
Even Microsoft which has a history of supporting legacy items (looking at you Internet Explorer) is deprecating TLS 1.0 and TLS 1.1 in many of its products (and in some cases outright disabling). And just in case it wasn't clear, all versions of SSL are insecure as well. Fully updated installs of Windows 10 and macOS, unfortunately, still leave TLS 1.0 enabled for client and server connections.
Chrome, Safari, Firefox, and Edge dropped support for anything less than TLS 1.2 a while back now. If you're using an up-to-date version of one of those browsers you are good-to-go there (note this doesn't mean other applications on your system won't use TLS 1.0/1.1).
Vendors are currently working on adoption and I hope that very soon TLS 1.3 will replace TLS 1.2. Cloudflare has a fantastic blog post on TLS 1.3 covering its design changes, benefits over TLS 1.2, and overall a ton of great information on the topic. Once you're done here I highly encourage checking it out.
If this were a couple years ago, this section would have been A LOT longer. Thankfully now, most everyone agrees just using TLS 1.2 is the way to go. Now on to cipher suites where things are...less decisive, let's say.
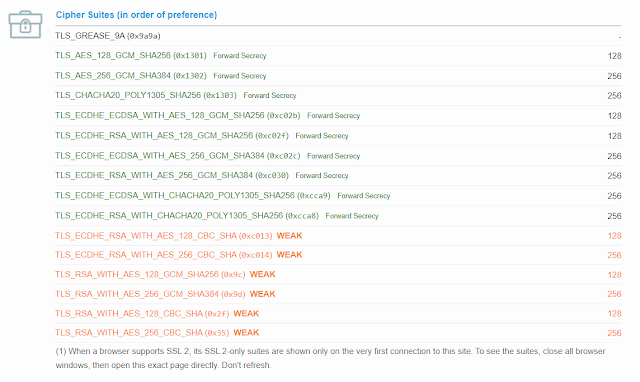
Secure Cipher Suites
- Prefer ephemeral keys over static keys (i.e., prefer DHE over DH, and prefer ECDHE over ECDH). Ephemeral keys provide perfect forward secrecy.
- Prefer GCM or CCM modes over CBC mode. The use of an authenticated encryption mode prevents several attacks (see Section 3.3.2 for more information). Note that these are not available in versions prior to TLS 1.2.
- Prefer CCM over CCM_8. The latter contains a shorter authentication tag, which provides a lower authentication strength.
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xC0, 0x2C)
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xC0, 0x30)
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x00, 0x9F)
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x00, 0x39)
- TLS_DH_DSS_WITH_AES_256_GCM_SHA384 (0x00, 0xA5)
- TLS_DH_RSA_WITH_AES_256_GCM_SHA384 (0x00, 0xA1)
References
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-52r2.pdf
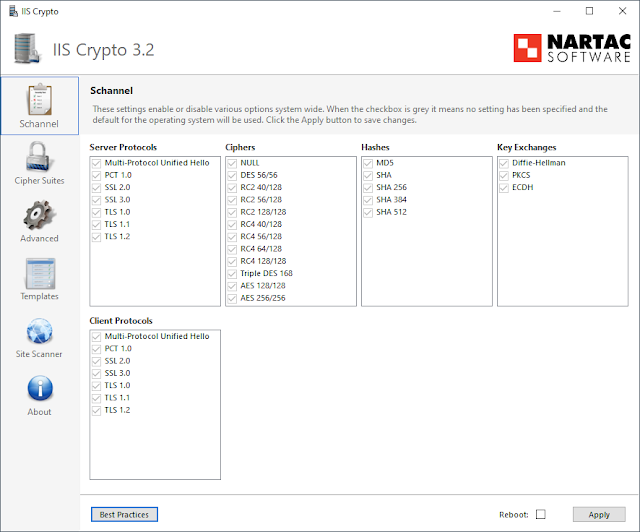
https://docs.microsoft.com/en-us/windows/win32/secauthn/cipher-suites-in-schannel
https://blog.cloudflare.com/rfc-8446-aka-tls-1-3/
https://blog.cloudflare.com/do-the-chacha-better-mobile-performance-with-cryptography/
https://eprint.iacr.org/2007/472
https://docs.microsoft.com/en-us/windows/win32/secauthn/protocols-in-tls-ssl--schannel-ssp-
https://support.apple.com/guide/deployment-reference-macos/network-security-apd1775f8cbb/web


Comments
Post a Comment